The Software Supply Chain Security Platform
Delivering visibility into software supply chain risks, starting with the most comprehensive SBOM.

Protect your software supply chain end-to-end. Devs can ensure that open-source components, CI/CD workflows, and release pipelines are safe. Plus, the SOC gets greater visibility of the entire build process, bolstering your organization's last line of defense.
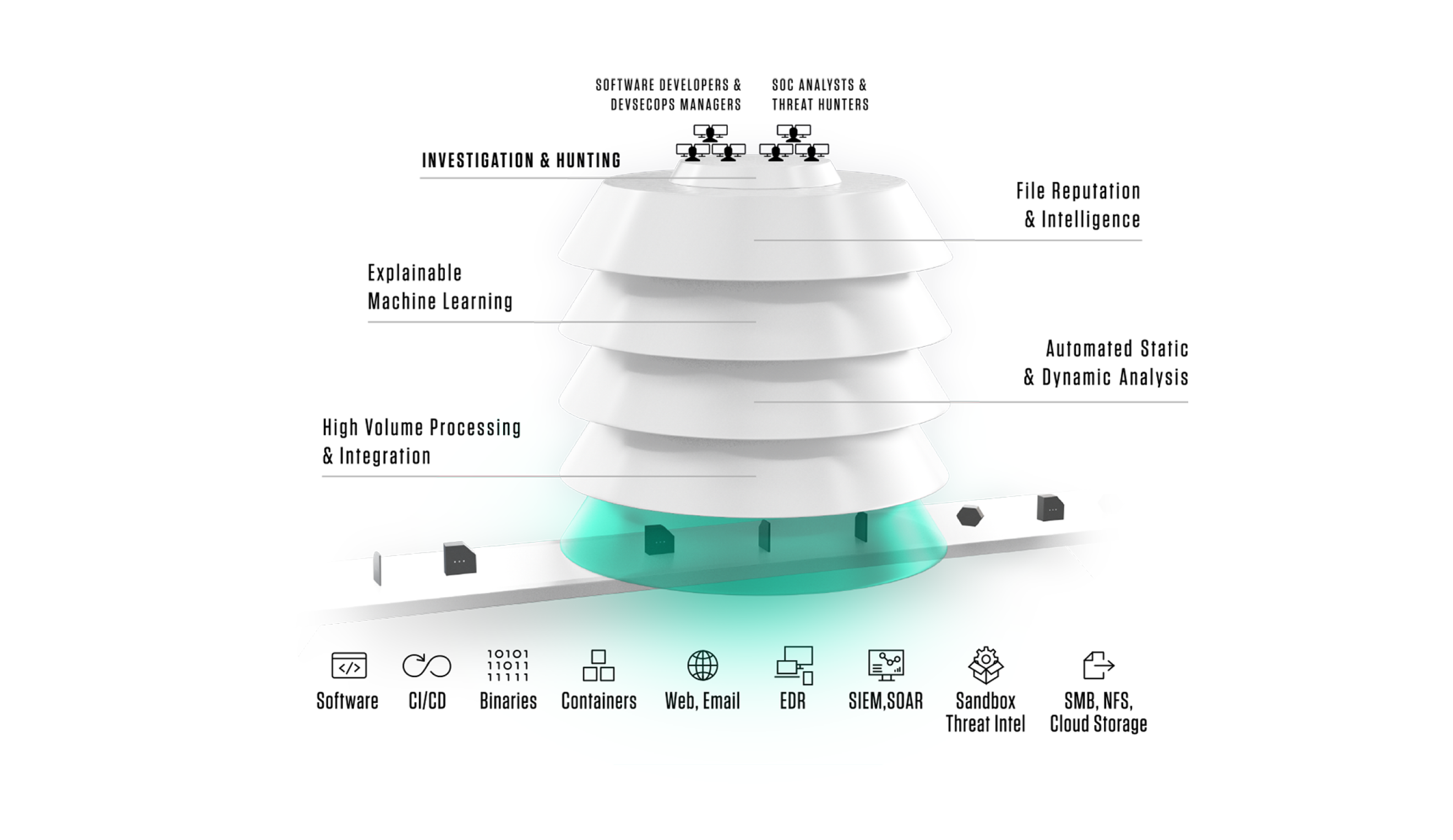
A machine learning hybrid cloud platform that harvests thousands of file types at scale, speeds threat detection through machine learning binary analysis, and continuously monitors a comprehensive index of goodware and malware files for future threats.


Software supply chain security protection for CI/CD workflows, containers, and release packages that enables DevSecOps teams to release software with confidence.
TitaniumCloud is a threat intelligence solution providing up-to-date file reputation services, threat classification and rich context on tens of billions of goodware and malware files. Files are processed using ReversingLabs File Decomposition Technology. A powerful set of REST API query and feed functions deliver targeted file and malware intelligence for threat identification, analysis, intelligence development, and threat hunting services.

ReversingLabs Cloud Deep Scan is a cloud file share threat intelligence solution that continuously scans Amazon Web Services S3 buckets for threats. This solution provides quality classification for large files (up to 10GB), allowing IT and SOC teams to quickly prioritize malicious files for investigation and remediation. It provides file reputation and threat analysis. ReversingLabs Cloud Deep Scan enables file-based business workflows with easy-to-understand file classification based on one of the largest repositories of known goodware and malware files.


TitaniumScale helps enterprises assess millions of files from web traffic, email, file transfers, endpoints or storage. The solution uses unique ReversingLabs File Decomposition Technology to extract detailed metadata, add global reputation context and classify threats. It automatically acquires files by integrating with email gateways, intrusion detection systems, firewalls and other devices. Results feed into SIEM, SOAR, and analytics platforms to provide visibility and enriched data for remediation and advanced hunting.
The A1000 provides advanced hunting and investigations through the TitaniumCore high-speed automated static analysis engine, and integrates with file reputation services to provide in-depth rich context and threat classification across thousands of file types based on a comprehensive repository of goodware and malware. It supports visualization, APIs for automated workflows, global and local YARA Rules matching, and integration with third-party sandbox tools.


ReversingLabs has developed a set of Open-Source YARA rules built with the purpose of delivering zero false positives. Achieving the highest level of quality requires a rigorous quality assurance test. Each rule must be run against ReversingLabs industry leading cloud repository of 25B unique binaries. Only the rules that meet the strictest of criteria are considered for GitHub.

Learn below how a unified software supply chain security platform enables both Dev and SOC teams to release software and respond to incidents with speed and confidence.

Knowing what is in your software package is the first step in securing your software supply chain. Get your free Software Bill of Materials (SBOM) report now.

ReversingLabs automates software supply chain security assessments, policy control and component visibility required by organizations acquiring, deploying and managing third-party applications. It empowers Third-Party Risk Management, Procurement, and IT teams to safely accept third-party software and future updates.

ReversingLabs assesses software components, releases and containers for malware, tampering, and other software supply chain threats and exposures. Development and Application Security teams use ReversingLabs to prioritize threat remediation, protect software integrity, and improve security quality to confidently release software that maintains customer trust.

Internal data, logs, and alerts possess vital insights into active and evasive threats. But alert volume, false positives/negatives, and a lack of clarity has stretched SOC teams to the max inhibiting them from making quick and informed decisions. ReversingLabs provides the right data in the right place to accelerate and prioritize alert triage.

Automate response to incidents with deep threat context to support confident analysis and action. ReversingLabs eliminates manual research and reverse engineering steps, while surfacing local intelligence in real-time - integrated seamlessly with incident response or SOAR system - arming you with information you can trust in order to respond fast.

ReversingLabs provides comprehensive, automated static analysis on files entering an organization. This rich, highly relevant file intelligence enhances correlation and visibility of malware, enriching any SIEM or SOAR, and promotes a more effective and efficient malware identification and incident response process.

Cloud file share and storage systems represent powerful productivity and collaboration environments, but they can also serve as an unintended distribution platform for malicious files and software. ReversingLabs scans cloud file sharing and synchronization systems for malware and suspicious content to isolate threats before they spread.

Detecting emergent ransomware attacks in their early stages is critical to prevent catastrophic loss of data and business interruptions.

Growing demand for local malware analysis capabilities continue to advance the need for a Malware Lab, a centralized malware analysis service organization that provides a single point of contact across the digital business for escalated workflows

The volume of evasive attacks now requires threat hunting to be a continuous, 24x7 process. But many hunting and threat intelligence teams are bogged down in manual research processes that lack the adequate tooling to be effective.

ReversingLabs automates and accelerates threat detection by unpacking all inbound files using static analysis, not executing files, and analyzes them for hidden malware indicators — leaving sandboxes to process only critical files of interest — faster.
ReversingLabs integrates with email platforms, gateways and SMTP relay points to rapidly analyze and detect advanced attacks, delivering real-time analysis of all email content and inbound traffic.

ReversingLabs integrates with endpoint detection and response (EDR) solutions to instantly and confidently identify files as malicious — without execution.

ReversingLabs APIs and Feeds integrate with threat intelligence platforms (TIPs), connecting actionable malware indicators with existing workflows

Modern SOC teams require agility and accuracy to detect and respond to threats. Learn about how ReversingLabs enhances Microsoft Sentinel — and start a free trial.