Overview
OpenText™ Cybersecurity Cloud
OpenText™ Cybersecurity Cloud helps organizations of all sizes protect their most valuable and sensitive information. Our portfolio of end-to-end cybersecurity solutions offers 360-degree visibility across an organization, enhancing security and trust every step of the way.
The OpenText Cybersecurity Cloud benefits

Implement Zero Trust across attack surfaces
Reduce business and financial risk through multivector protection against attack surfaces.

Minimize downtime
Investigate threats, understand their impact, and recover data within minutes.

Maintain privacy and security compliance
Leverage real-time contextual threat intelligence to stay resilient and compliant

Featured products
OpenText Cybersecurity Cloud products secure organizations while protecting data to support customers, employees and investors regardless of cyber challenges.
Application Security
Seamlessly integrate application security into any tool, anywhere in the SDLC.

OpenText™ Fortify™ Aviator
Secure smarter, not harder with AI code analysis and code fix suggestions

OpenText™ Fortify™ On Demand
Unlock security testing, vulnerability management, and tailored expertise

OpenText™ Fortify™ Static Code Analyzer
Find and fix security issues early with the most accurate results
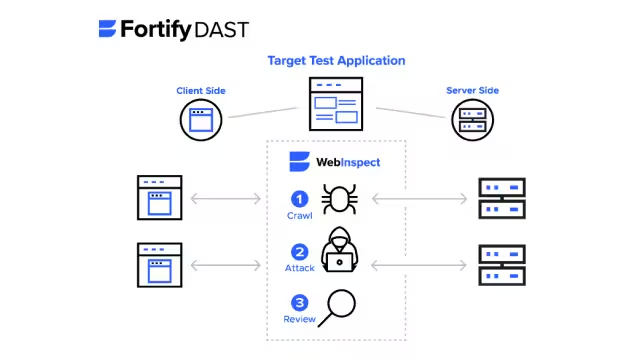
OpenText™ Fortify™ WebInspect
Identify vulnerabilities in deployed web applications and services

OpenText™ Debricked™
Take full control of security, compliance and health
Identity Governance and Administration
Deliver the right access to the right users with the least amount of friction.

OpenText™ NetIQ™ Access Manager
Enable single sign-on and access across mobile, cloud, and legacy platforms

OpenText™ NetIQ™ Identity Governance
Protect all data with simplified compliance and user access review processes

OpenText™ NetIQ™ Privileged Account Manager
Centralize control over admin accounts across your entire IT landscape

OpenText™ NetIQ™ Identity Manager
Simplify identity lifecycle management to ensure secure resource access

OpenText™ NetIQ™ Advanced Authentication
Enable passwordless and multifactor authentication for protection

OpenText™ NetIQ™ Data Access Governance
Gain insights, secure unstructured data, and prevent unauthorized access
Data Privacy and Protection
Understand and secure data to reduce risk, support compliance, and govern data access.

OpenText™ Voltage™ Fusion Platform
Discover and protect your most valuable data with our end-to-end data security

OpenText™ Voltage™ SecureData
Protect high-value data while keeping it usable for hybrid IT

OpenText™ Voltage™ Structured Data Manager
Manage structured data over its lifecycle
Digital Investigations and Forensics
Get to the truth faster with reliable investigation results.

OpenText™ Encase Forensic
Close cases quickly with reliable digital forensic investigation results

OpenText™ EnCase Endpoint Investigator
Discover behaviors that put corporate assets at risk

OpenText™ EnCase Endpoint Security
Detect, analyze, triage and respond to malicious attacks

OpenText™ EnCase Information Assurance
Conduct defensible data collection and ensure effective information governance
OpenText™ EnCase Mobile Investigator
View, analyze and report on mobile evidence involved in an investigation

OpenText™ Tableau Forensic
Digital forensic imaging for law enforcement and corporate investigations
Threat Intelligence
Discover actionable insights, from threat detection to risk management.

BrightCloud® Threat Intelligence Services
Powerful AI/ML backed insights available via modular services
Threat Detection and Response
Harness unparalleled network visibility to efficiently hunt for and defend against threats.

OpenText™ Network Detection & Response
Harness unparalleled network visibility to efficiently defend against threats

OpenText™ ArcSight™ Enterprise Security Manager
Real-time threat detection and response from a powerful, adaptable SIEM

OpenText™ ArcSight™ Intelligence
Detect, investigate, and respond to threats that may be hiding

OpenText™ ArcSight™ cyDNA
SaaS-based global signal analytics to discover, define, and contextualize threat

OpenText™ ArcSight™ Recon
Enhance your SOC with a fast, user-friendly log management and threat hunting platform
Information Management at Scale
OpenText
Cybersecurity Cloud
Smarter, simpler protection
79%
of organizations experienced a ransomware incident in one year
Solutions Offered
Explore our wide range of cutting-edge technologies.
The practice of protecting email accounts and communications from unauthorized access, loss, or compromise.
Threat intelligence is the process of identifying and analysing cyber threats. Refer to the data collected on a potential threat or the process of gathering, processing and analysing that data to better understand threats.
A set of technologies, policies, and best practices that protect data, applications, and infrastructure in cloud environments.
MFA vs 2FA. So, two-factor authentication (2FA) requires users to present two types of authentication, while MFA requires users to present at least two, if not more types of authentication.
A framework of business processes, policies and technologies that facilitates the management of digital identities.
A security process that verifies a device's identity to ensure it's authorized to access a resource or perform an action.
Backup and DR service enables users to protect backups against malicious attack and to recover in new environments.
Law Enforcement Organization Technologies deliver advanced solutions designed to support law enforcement agencies and investigative teams in their mission to combat cybercrime, safeguard communities, and uphold justice. These tools enable efficient evidence collection, secure data analysis, and seamless case management, ensuring investigations are conducted with accuracy, integrity, and compliance with legal and regulatory standards.
