
AI-Powered
Threat Intelligence
Operations and
Cyber Risk Quantifications
Make threat intelligence, security operations, and cyber risk management teams more effective, efficient, and collaborative with AI-powered solutions that enable the operationalization of high-fidelity threat and risk insights.
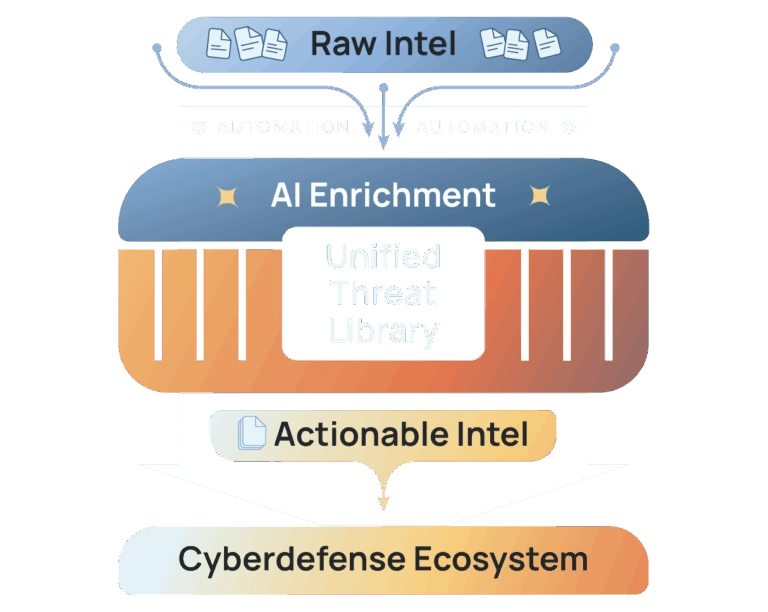
Unlock All Your Security Data
Federated search, correlation, and analysis puts intelligence and context at the point of decision
Operationalize Threat Intelligence
Put high-fidelity threat intelligence at the core security operations for more effective cyber defense
Quantify Cyber Risk
Prioritize security investments and defensive actions based on the greatest risks to your business
Intelligence Your Teams Will Love
Produce and share relevant, actionable threat intelligence
Cyber Threat Intelligence Analyst
The increasing volume and velocity of indicators, reports, and other data that come in every day can feel impossible to process and analyze.
ThreatConnect automatically aggregates, normalizes, and adds context to all of your intel sources into a unified repository of high fidelity intel for analysis and action.
Threat intelligence collection, analysis, and dissemination requires too much manual work.
Threat intelligence collection, analysis, and dissemination requires too much manual work.
It’s difficult to clearly and efficiently communicate with other security teams and leadership.
ThreatConnect makes it fast and easy for you to disseminate critical intel reports to stakeholders.
See how the ThreatConnect Platform can evolve your CTI into TI Ops.
A Threat Intelligence Platform That Drives Your Defense
Secure and defend your enterprise with a unified source of relevant threat intelligence.
SOC Analyst
Detect, investigate, and respond to security incidents effectively using a single source of relevant, high-fidelity threat intelligence.
Incident Responder
ThreatConnect provides business-relevant threat intel and context to help you reduce response times and minimize the blast radius of attacks.
Threat Hunter
ThreatConnect’s AI-powered global intelligence and analytics helps you find and track the threat actors targeting your industry and peers.
Context Without the Clicks
Polarity overlays real-time threat intelligence and context into any tool, from any tool: it’s like Ctrl+F for your security stack
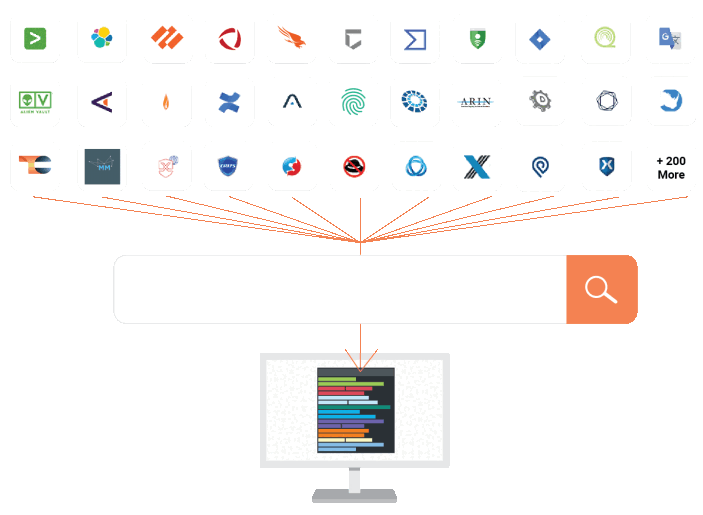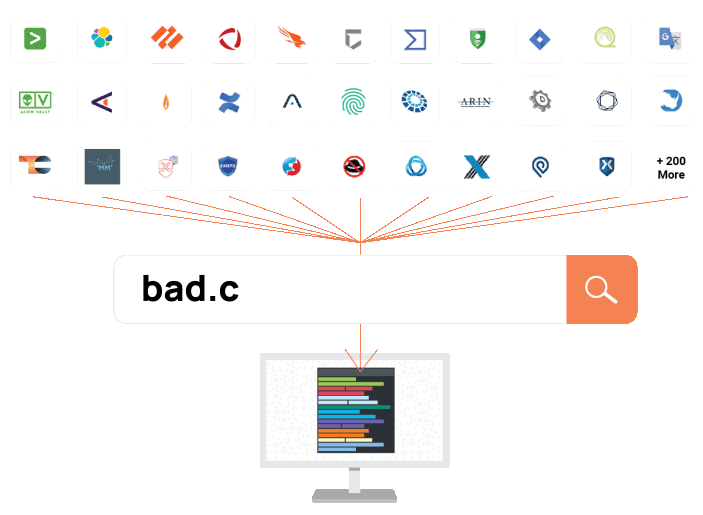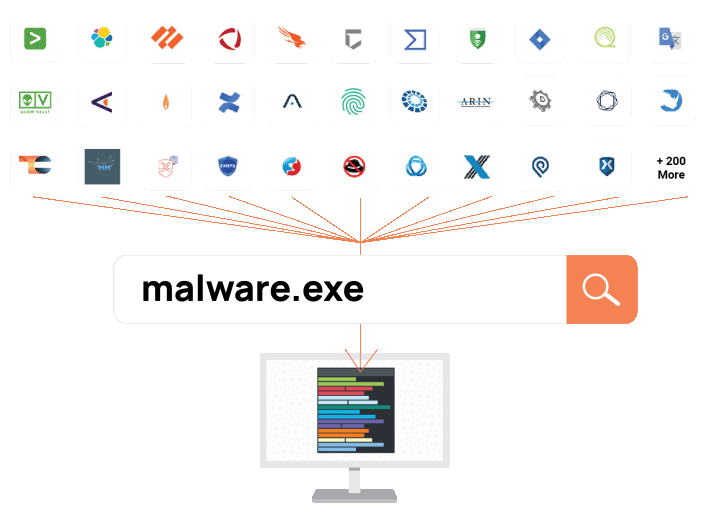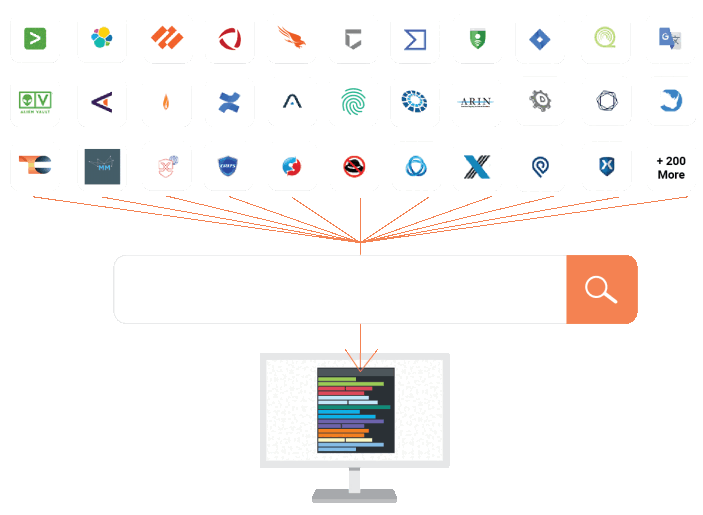
SIEMs
Quickly triage alerts by adding real-time threat context, correlating logs with known IOCs, and filtering noise through enrichment scoring to reduce alert fatigue.
SOARs
Streamline response by triggering playbooks in-place, using enrichment scores for escalation decisions, and capturing analyst input to enhance future automation.
Vulnerability Management
Prioritize vulnerabilities by active threats and financial risk, use CAL enrichment to spot real-world exploits, and cut ticket noise by filtering low-priority findings.
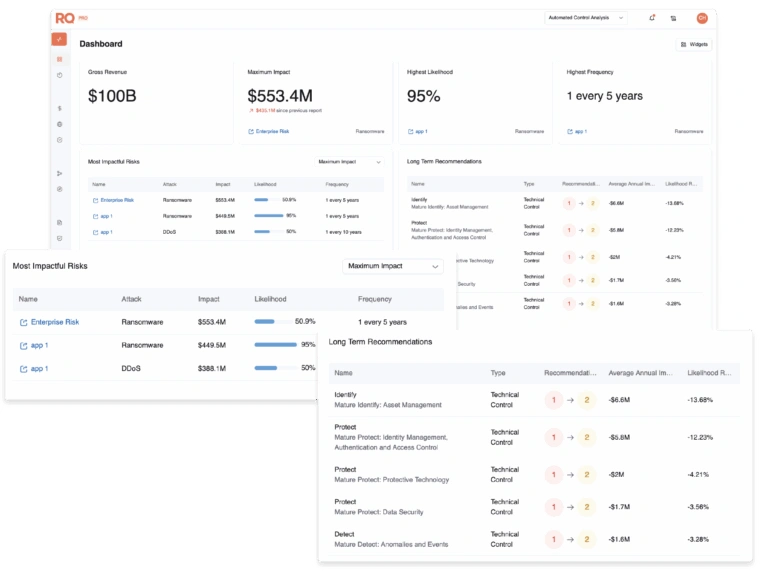
Cyber Risk Quantification from the Board to Byte
Translate threats, vulnerabilities, and control gaps into financial terms — helping leaders to prioritize defense, justify investments, and align teams.
Networks
Ingest firewall and NDR data from multiple sources, then model exposure using traffic patterns and threat behavior.
Applications and Workloads
Pull data from tools like ServiceNow and SureCloud, then assess how controls apply across services, apps, and workflows.
Data
Power CRQ with telemetry from your stack by ingesting data from ThreatConnect, Zscaler, Snowflake, and more, then fueling modeling with enriched intel and asset metadata.
Threat and Risk Intelligence Solutions
Elevate Your Threat Intelligence
Move from reactive to proactive security by operationalizing your cyber threat intelligence.
Elevate Your Threat Intelligence
Move from reactive to proactive security by operationalizing your cyber threat intelligence.
Modern Cyber Threat Intel
Threat Intelligence Operations requires a modern approach. Shift your approach to cyber threat intelligence with an Evolved Threat Intel Lifecycle.
ThreatConnect is a powerful tool that can help organizations to improve their security posture and protect themselves from cyber threats.
Solutions Offered
Explore our wide range of cutting-edge technologies.
Threat intelligence is the process of identifying and analysing cyber threats. Refer to the data collected on a potential threat or the process of gathering, processing and analysing that data to better understand threats.
