
Identity Security Platform
Secure identities – human and machine – from end-to-end

Defend Against Attacks
Protect against compromised identities and credentials

Satisfy Audit & Compliance
Protect against compromised identities and credentials

Enable the Digital Business
Protect against compromised identities and credentials

Drive Operational Efficiencies
Protect against compromised identities and credentials
Privilege
Enforce Least Privilege
Apply least privilege security controls. Protect privileged access across all identities, infrastructure and apps, from the endpoint to the cloud.

Defend Against Attacks
Protect against the leading cause of breaches — compromised identities and credentials.

Enable the Digital Business
Deliver digital experiences that balance security and a frictionless experience.

Satisfy Audit and Compliance
A unified solution to address identity-oriented audit and compliance requirements.
Access Management
Enable access across any device, anywhere just the right time
Secure Everywhere
When everything is transforming digitally – from your industry to the threats you face – you need Identity Access Management (IAM) solutions designed to outpace any security risks that challenge your ability to compete.

Let Users In, Keep Threats Out
Consolidate key security technologies and simplify policy enforcement.

Secure Digital Confidence
Improve business agility to deliver great digital experience.

Protect Your Core
A privilege-centric approach to securing identities.

Support Remote
Give your distributed workforce the tools they need – without compromising security.
DevSecOps
Simplified the process of securing non-human identities across DevOps pipelines
Security at The Speed Of Innovation
Application code within the digital supply chain are an increasing target for sophisticated cyber attacks. With CyberArk, you can help ensure security across the DevOps pipeline while driving business agility and a frictionless experience for developers.

Enable the Digital Business
Keep application and automation tools secure without slowing down developer velocity.

Defend Against Attacks
Give applications easy access to the credentials they need, while keeping secrets out of reach for attackers.

Drive Operational Efficiencies
Reduce complexity and burden on developers while improving agility and protection of the business.
CyberArk Solutions
Identity and Access Management
When everything is transforming digitally – from your industry to the threats you face – you need identity Access Management (IAM) solutions designed to outpace any security risks that challenge your ability to compete.
Multi Factor Authentication (MFA) & 2 Factor Authentication (2FA)
Secure access to your entire organization with a broad range of secondary authentication methods
Single Sign On (SSO) & passwordless
Transform enterprise security and employee productivity with an end-to-end passwordless experience that goes beyond traditional authentication.
Priviliged Access Management (PAM)
Modernize your PAM program and provide defense-in-depth protection throughout your IT estate, in hybrid and multi-cloud environments. Explore new processes, policies, and controls to better reduce the risks of privileged access.
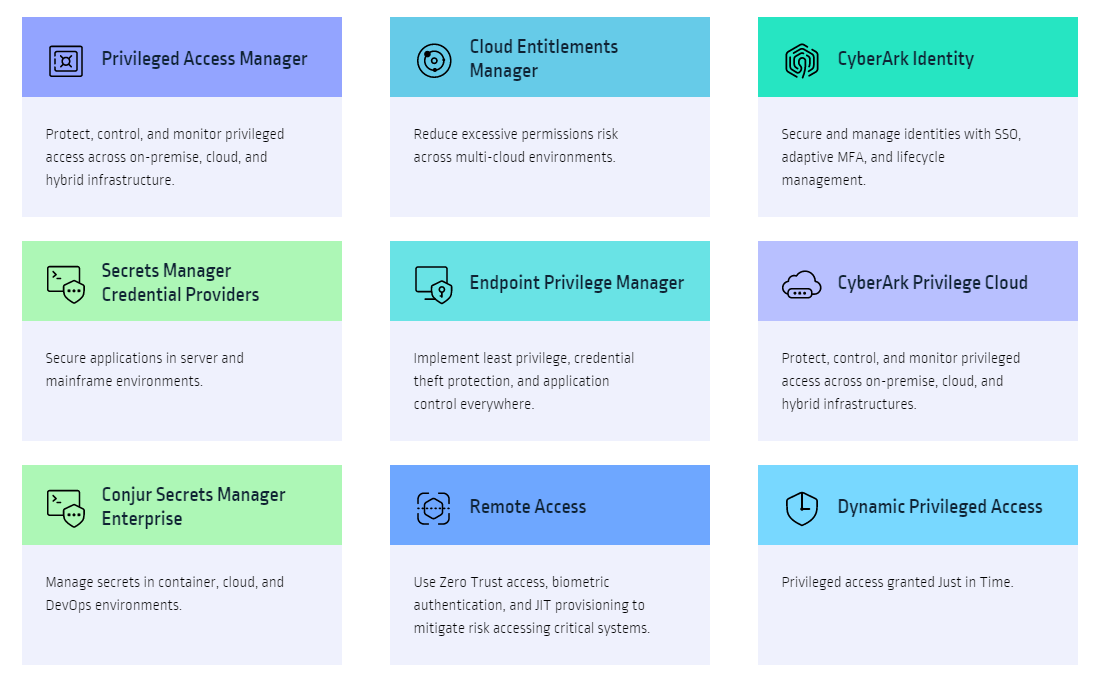
Solutions Offered
Explore our wide range of cutting-edge technologies.
MFA vs 2FA. So, two-factor authentication (2FA) requires users to present two types of authentication, while MFA requires users to present at least two, if not more types of authentication.
Simplify access and enhance security with SSO and passwordless technologies. Provides seamless login experience, secure access to application and improving efficiency accross the organization
A framework of business processes, policies and technologies that facilitates the management of digital identities.
A subset of IAM that allows you to control and monitor the activity of privileged users once they are logged into the system.
Learn More About CyberArk Products
Virtual Graffiti is an authorised online reseller of CyberArk solutions. We offer expert advice, tailored packages, and competitive pricing across Australia.
 Visit the CyberArk Cyberstore
Visit the CyberArk Cyberstore
