Attackers operate in runtime. Your AppSec should, too
Born from DAST pioneers Netsparker and Acunetix, now enhanced with ASPM capabilities from Kondukto, Invicti delivers the only proof-based application security platform that finds, validates, and prioritizes real vulnerabilities before attackers can exploit them.
Get a demo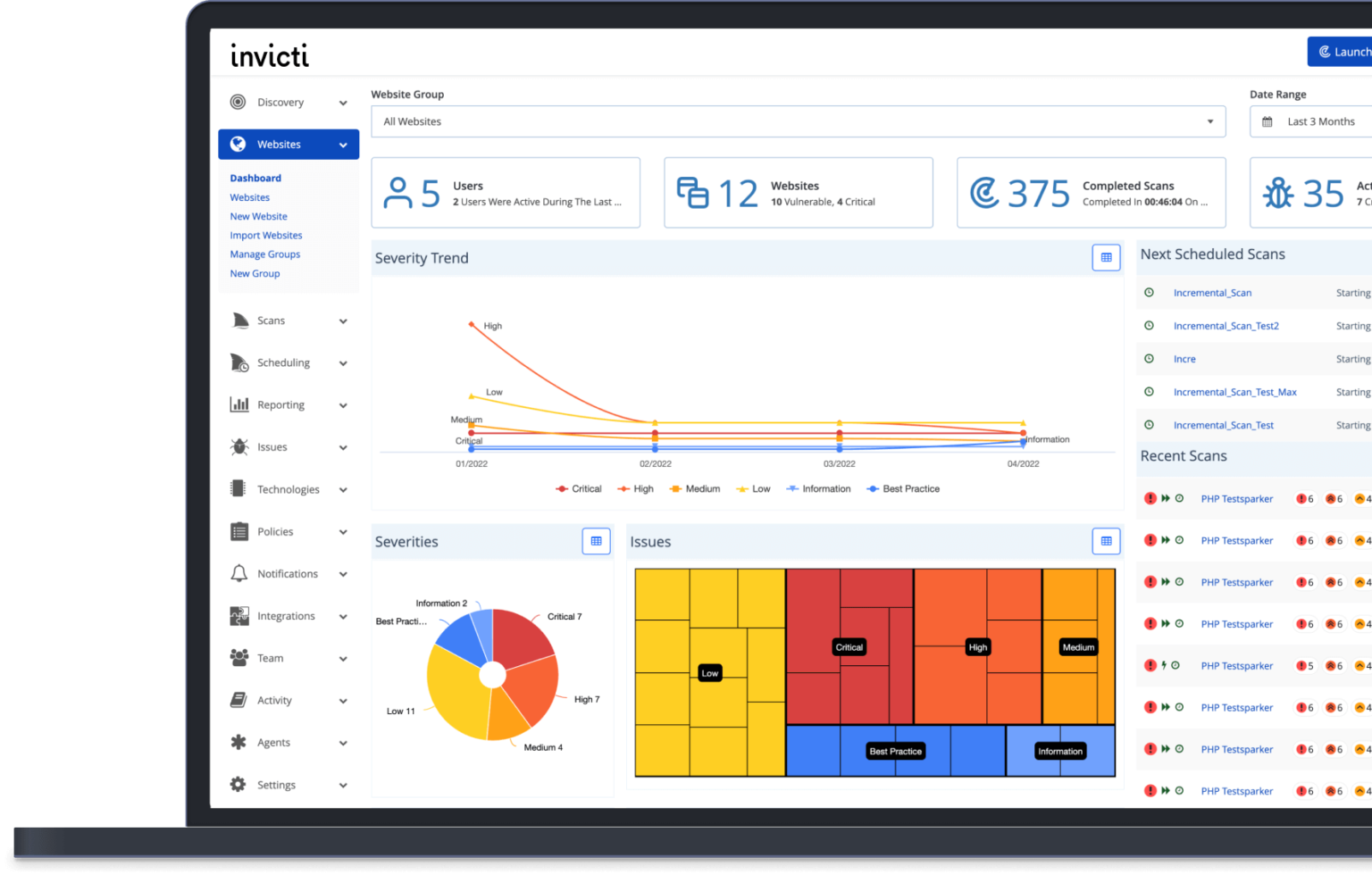





Why Prioritize Dast
Alert Fatigue is a Virus. Proof-based Scanning is the Cure
Legacy ASPMs organize the chaos—we eliminate it. We validate every vulnerability and
only surface real, exploitable risks. No noise. Just signal.
Without complete visibility into your apps, vulnerabilities, and remediation efforts, it’s impossible to prove you’re doing everything you can to reduce your company’s risk.
- Find all your web assets — even ones that have been lost, forgotten, or created by rogue departments.
- Scan the corners of your apps that other tools miss with our unique dynamic + interactive (DAST + IAST) scanning approach.
- Always know the status of your remediation efforts, through Invicti or native integrations with your issue tracking and ticketing software.

Industry-leading DAST, Powering a Unified Platform
Other AppSec providers have bolted on DAST capabilities. Invicti is the only platform built with DAST at its core. That means smoother integrations, more dynamic testing, 99.98% accuracy, and best-in-class security for enterprises.
Invicti’s industry-leading DAST engine delivers proof-based scanning with an industry-best 99.98% accuracy. Fully integrated into your SDLC, it scales effortlessly across teams and portfolios.
Learn More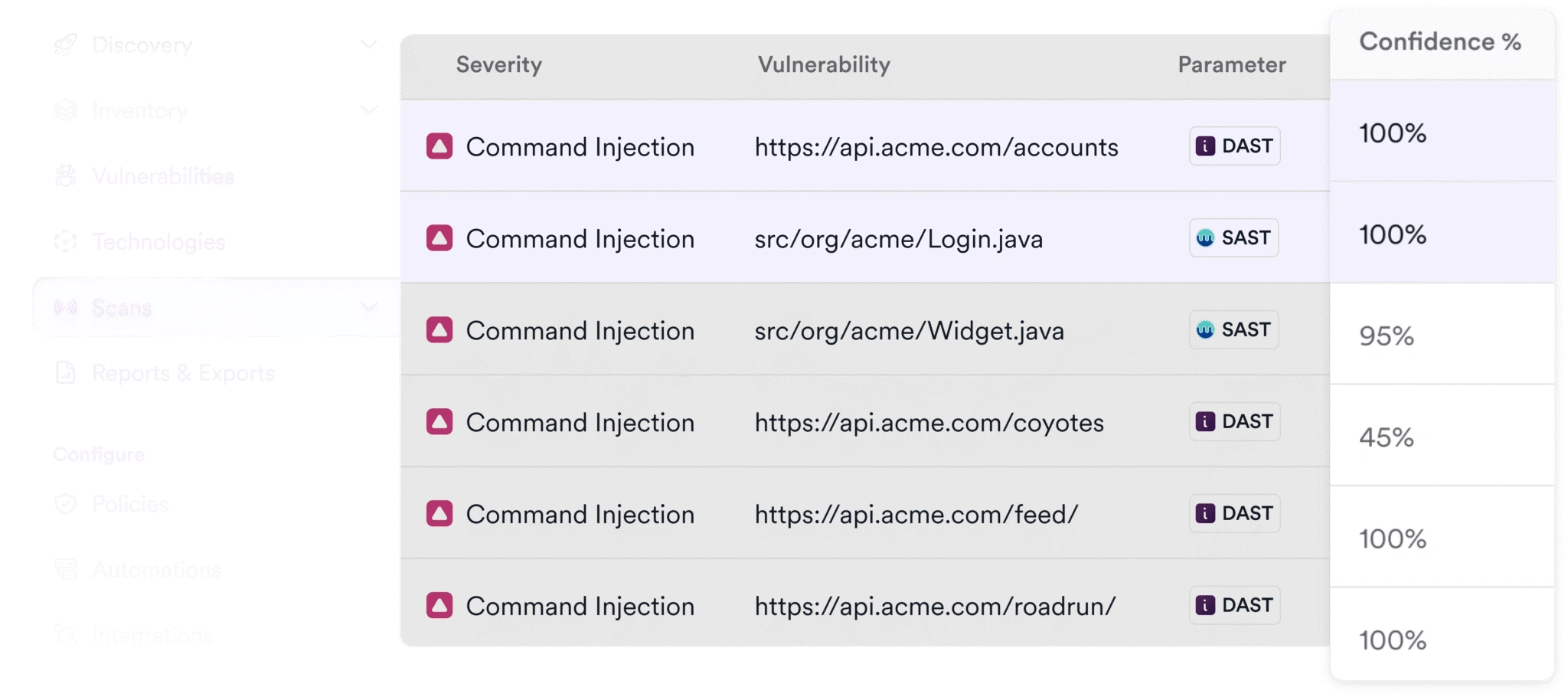
Invicti scans REST, SOAP, gRPC, and GraphQL APIs with the same depth and accuracy as web apps—validating vulnerabilities with proof. Documented or not, your APIs get full coverage, automatically.
Learn More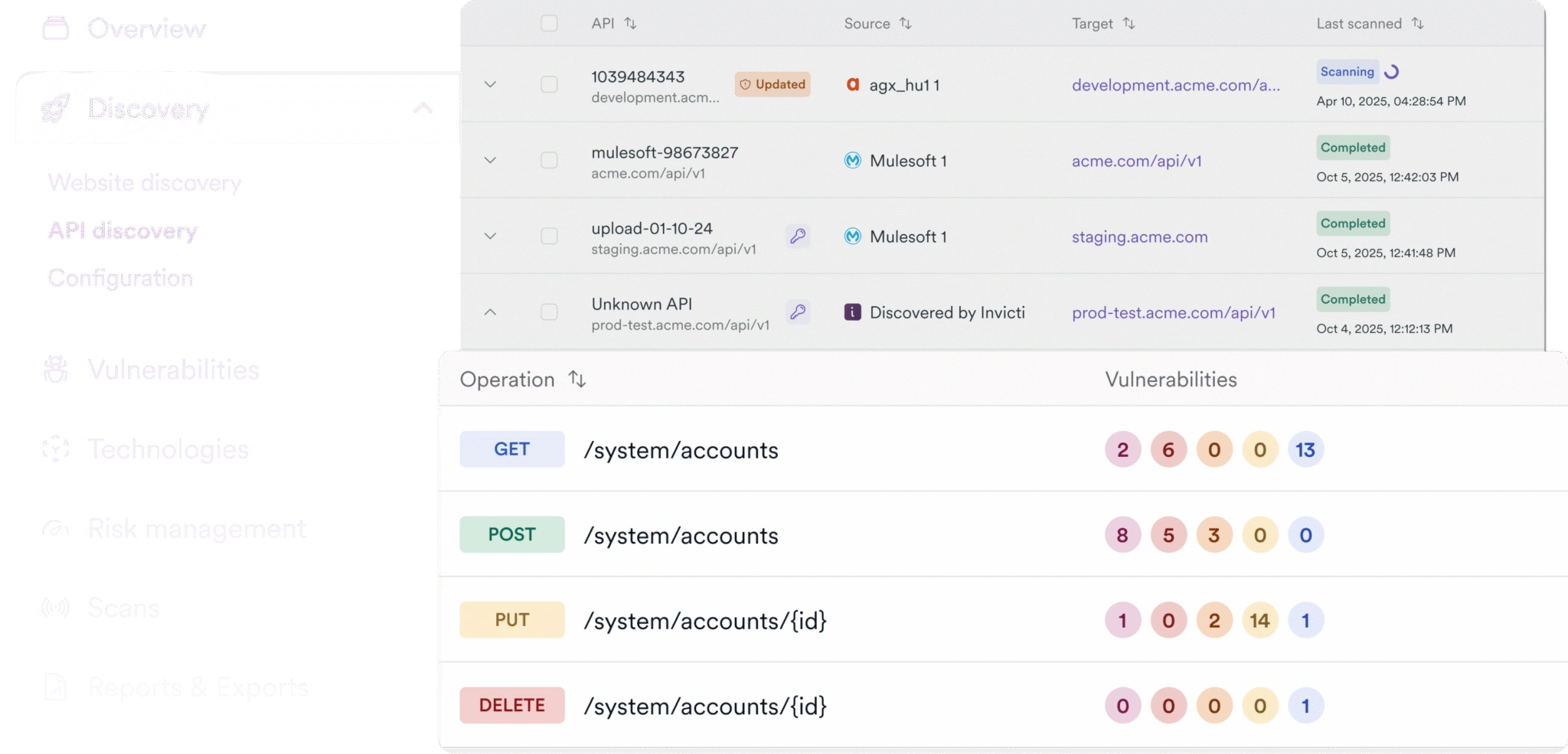
Invicti integrates with a leading SAST provider to give teams the best of both worlds: proactive static testing of all application code, paired with the proof-based validation of DAST. It’s SAST without the noise.
Learn More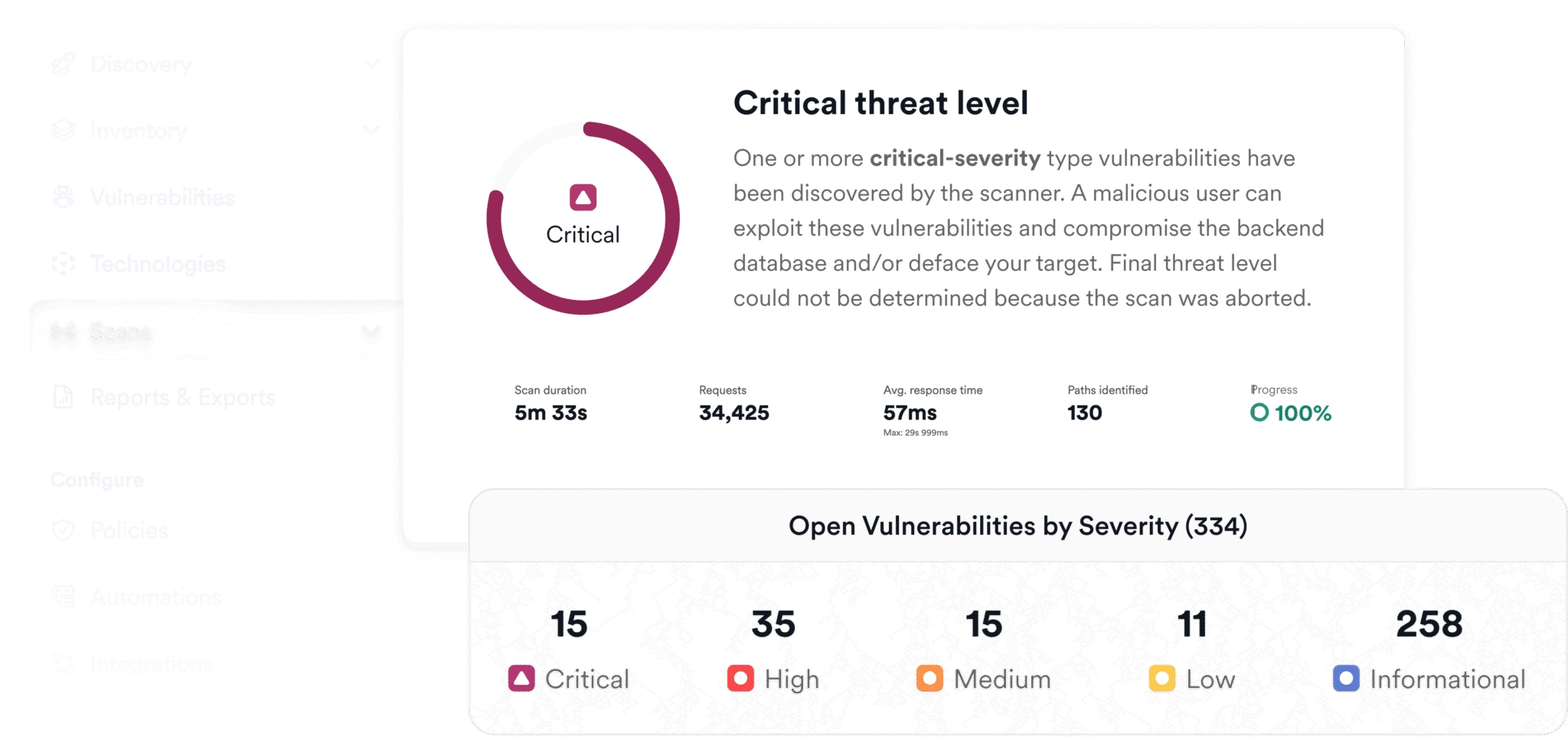
Invicti delivers integrated dynamic and static Software Composition Analysis, giving teams full visibility into open-source and third-party components. With runtime insight and deep code-level analysis, you get the context you need to fix issues faster.
Learn More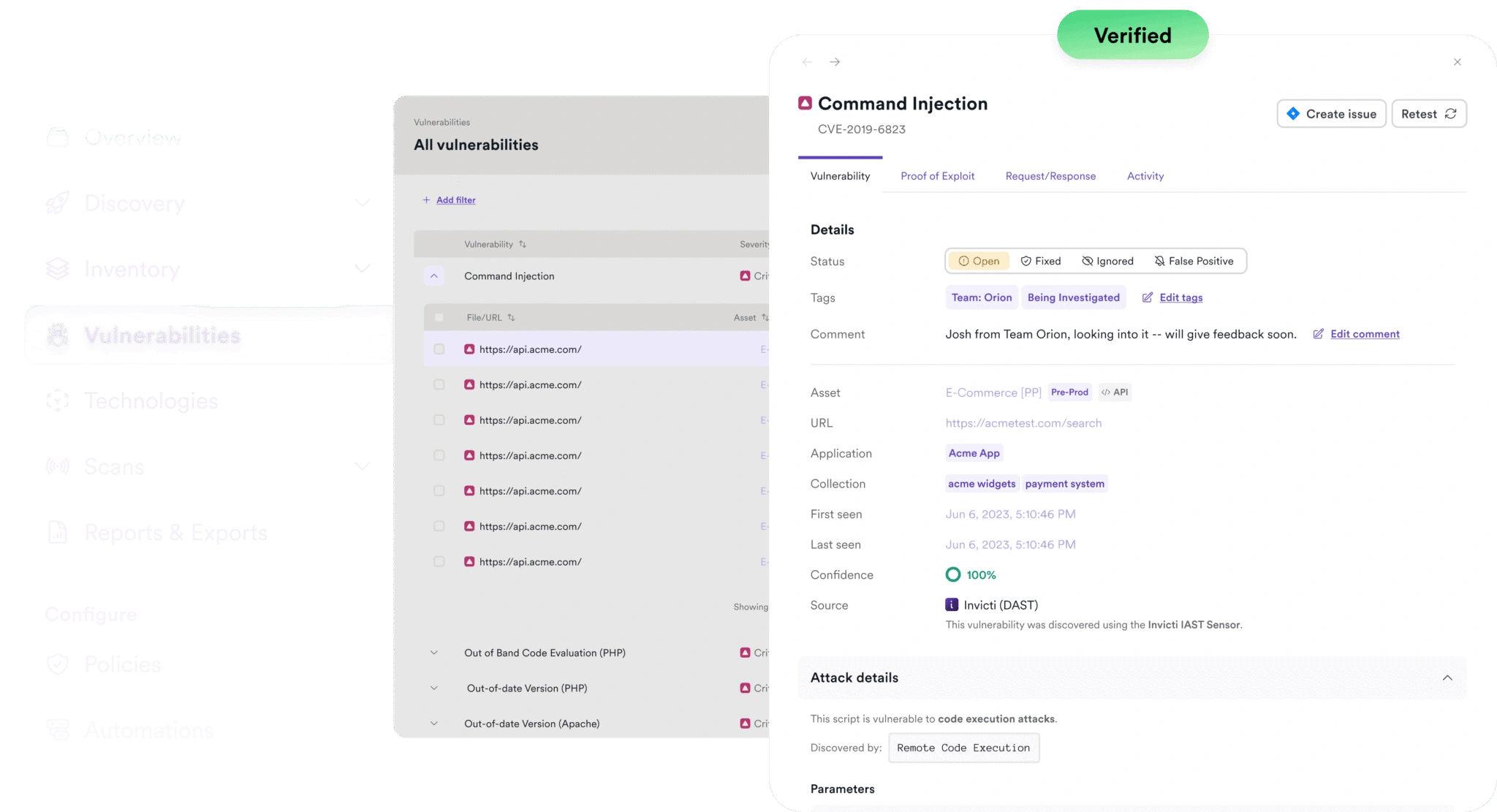
Invicti supports container image scanning across popular registries and Kubernetes environments so you can spot vulnerable components early, enforce policies, and ship secure containers at scale.
Learn More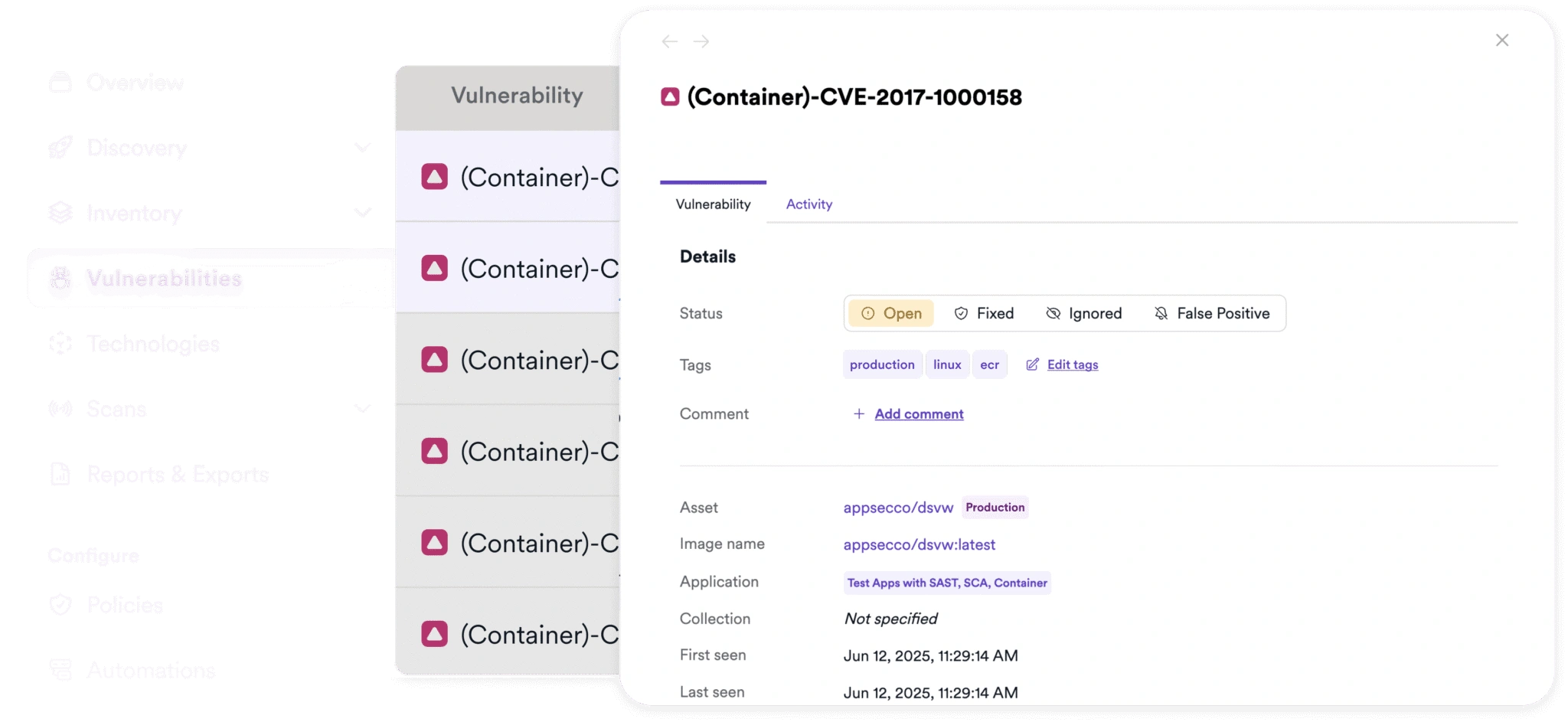
Invicti’s DAST-based ASPM unifies, validates, prioritizes, and acts on AppSec risk. Get a single source of truth with policy enforcement and audit-ready reporting.
Learn More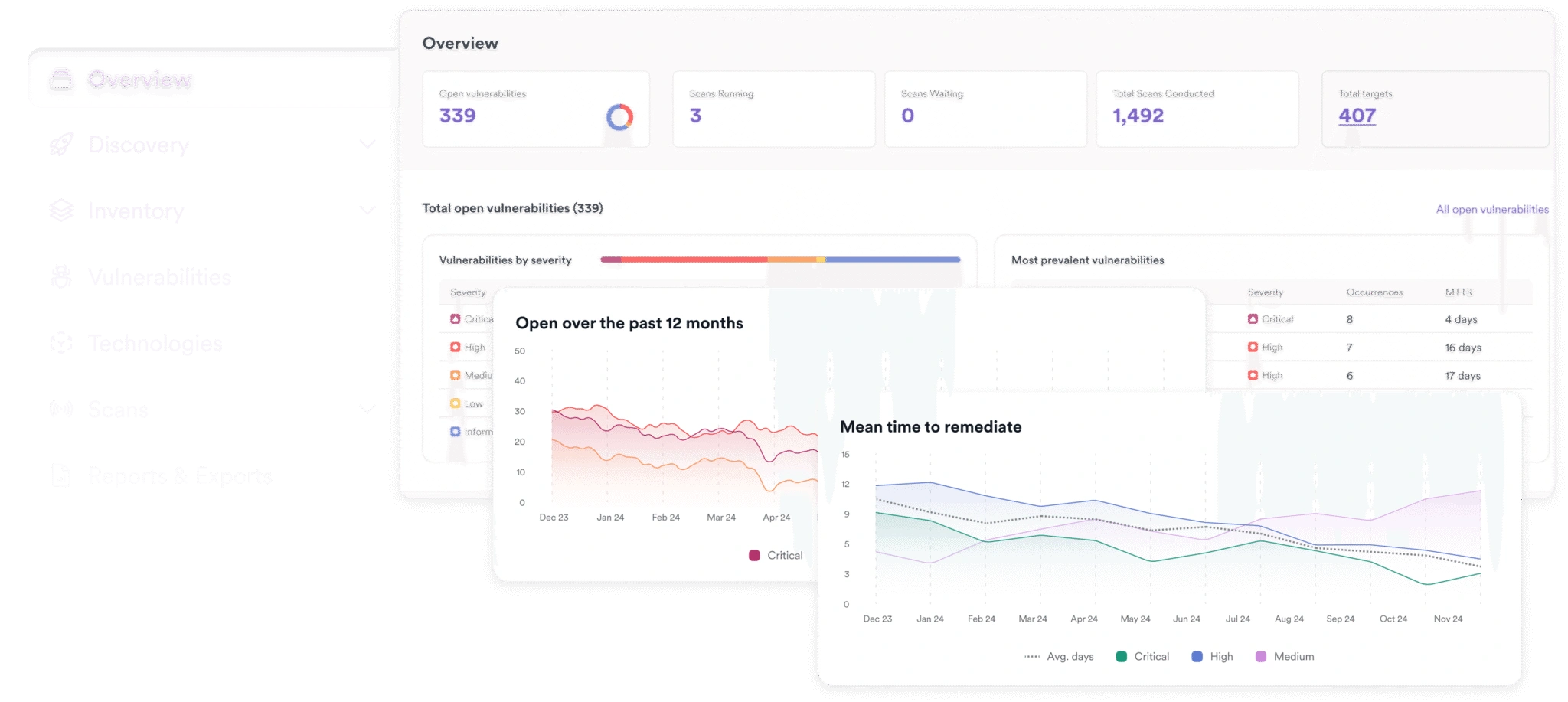
Automate security throughout your SDLC

Your security challenges grow faster than your team. That’s why you need security testing automation built into every step of your SDLC.
- Automate security tasks and save your team hundreds of hours each month.
- Identify the vulnerabilities that really matter — then seamlessly assign them for remediation.
- Help security and development teams get ahead of their workloads — whether you run an AppSec, DevOps, or DevSecOps program.
Manage risk like a team 10x your size
Security bottlenecks. Complex infrastructure. Your ever-growing list of vulnerabilities. It’s no surprise that teams like yours are overwhelmed by the sheer volume of work in front of them. Take control with scalable security testing that makes life easier for your security team.
- Reclaim the hundreds of hours your team spends chasing down false positives with features that confirm which vulnerabilities are real threats.
- Integrate security testing into your entire SDLC with powerful two-way integrations into the tools your development team already uses.
- Control permissions for unlimited users — no matter how complex your organization’s structure

World's Best DAST, Even Better with AI
The industry’s leading DAST engine continues to improve with AI innovations that are closing the gap between automated scanning and manual penetration testing.
Learn More8x
Faster Scanning
99.98%
Vulnerability Scanning Accuracy
70%
Acceptance Rate on AI Remediations
40%
More Vulnerabilities Found
Prevent vulnerabilities by producing more secure code

The longer a vulnerability lasts in your SDLC, the more costly it is to fix. Invicti helps you prevent vulnerabilities by showing your developers how to write more secure code in their existing environment. Because the easiest vulnerabilities to manage are the ones that never exist in the first place.
- Build security into your culture by integrating Invicti into the tools and workflows your developers use daily.
- Give developers access to actionable feedback that helps them produce more secure code — which means less work for your security team.
- Prevent delays with continuous scanning that stops risks from being introduced in the first place.
Trusted Across Industries
180+ Government agencies stay secure with Invicti
Government
Scale across environments, integrate into CI/CD workflows.
IT & Telecom

Innovate safely, accelerate development
Financial Services
Protect patient data, prove HIPAA compliance with built-in reporting.
Healthcare
50+ Integrations
Force-Multiply your Security Stack
Plug into the tools your devs use daily—from Jenkins to Jira to Slack. Invicti auto-assigns validated threats so your team can fix faster—without manual triage from security.









Invicti by the Numbers
3,600+
customers
Used in 115+
countries
800k+
web apps secured
300,000+
unique severe vulnerabilities found
Employees in 8
countries
15
languages spoken
The Finishing Blow for Flase Positives. Experience DAST-First AppSec Today.
Contact Us
Solutions Offered
Explore our wide range of cutting-edge technologies.
Application and API Security solutions safeguard applications and APIs from vulnerabilities, ensuring robust protection against attacks and unauthorized access.
