
Absolute Security Cyber Resilience Platform
We Stop Downtime
Resilient CISOs trust us to prevent and minimize business disruption and recover in minutes from cyber incidents
Contact UsFew Organizations Fully Recover from an Incident
$400B
annual cost of downtime
(Splunk + Oxford Economics, 2024)
$5.08M
average ransomeware/extortion cost
(IBM/Ponemon, 2025)
$4.88M
average data breach cost
(IBM/Ponemon, 2024)
61%
of supply chain breaches are from third-party vulnerabilities
(IBM/Ponemon, 2025)
+$670K
breach cost in shadow AI-heavy organizations
(IBM/Ponemon, 2025)
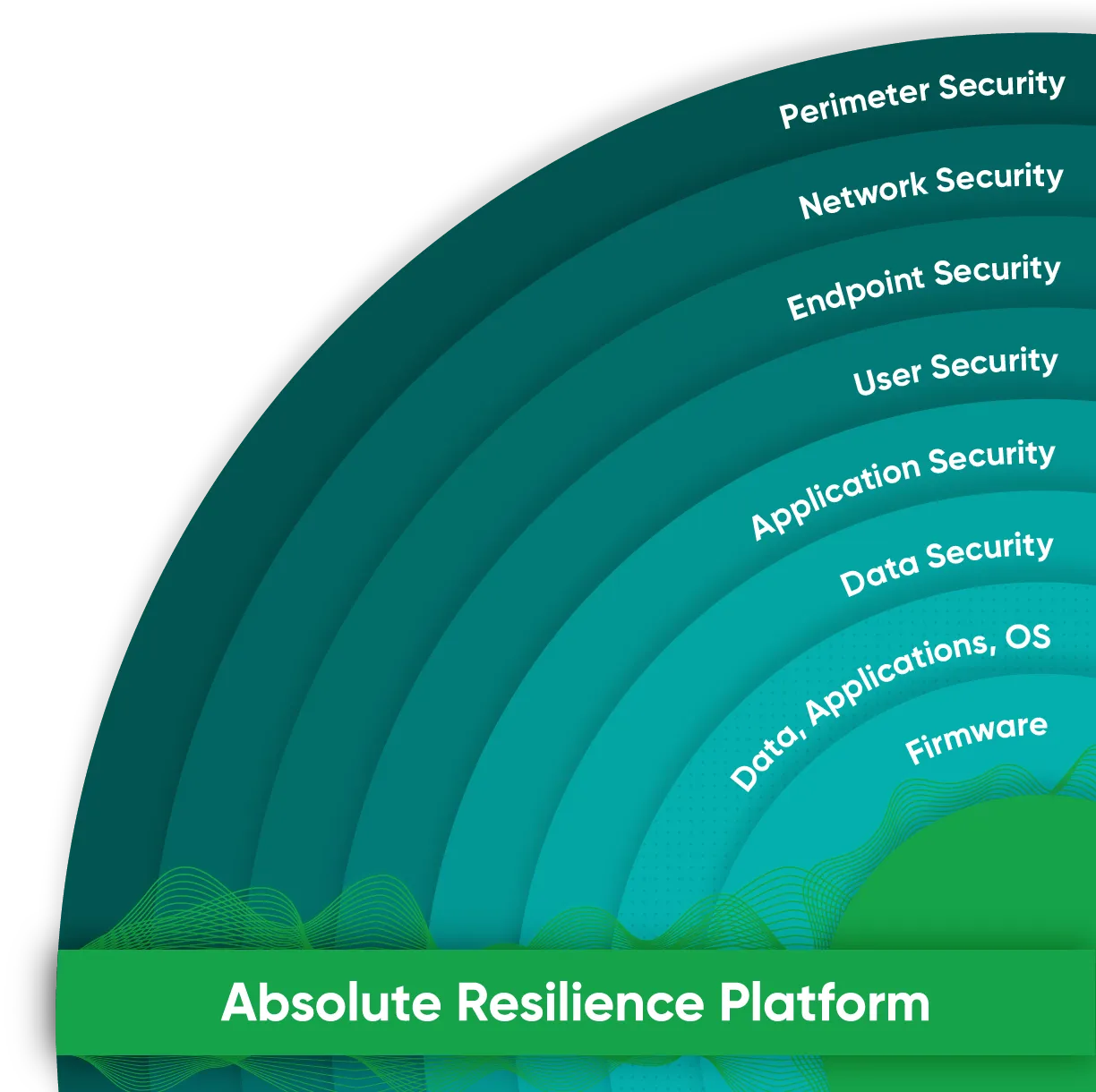
You need an enterprise platform that drives resiliency across your security stack
- Always ON
- Always CONNECTED
- Always PROTECTED
The Absolute Security Difference
- Persistence
Only Absolute Security's patented persistence technology is embedded in the firmware of over 600 million devices. - Resilience
Only Absolute Security creates an unbreakable connection between device firmware and the Absolute platform. - Intelligence
Only Absolute Security's platform and data uniquely delivers cyber resilience across your entire security stack.

The Absolute Platform
Secure Endpoint

Absolute Visibility
Gain foundational visibility across your endpoints to manage your devices, applications, users and data – on or off the corporate network. Track device hardware, software, sensitive data, usage, security vitals and more and be alerted to suspicious activity and compliance drift.

Absolute Control
Take action and respond to device or security risks. Create geofences to be alerted when devices breach approved boundaries, freeze devices when they are lost or stolen, perform a wipe or file delete to protect sensitive information, send messages to end-users and manage the supervisor password

Absolute Resilience
Harden endpoints and respond to IT or security incidents to reduce downtime. Monitor app health and self-heal critical security agents, query and remediate devices at scale, investigate and recover lost or stolen devices and restore compromised devices back to a fully trusted and compliant state after an incident

Absolute Resilience for Security
Efficiently manage the deployment of patches with minimal impact on users. Proactively scan for and deploy operating system and third-party patches, prioritize devices and patches with the highest risk to keep your environment secure and schedule patch deployments in maintenance windows to reduce end-user disruption and maintain productivity

Absolute Resilience for Automation
Consolidate patch and vulnerability management across your environment. Scan for and respond to operating system, software and security vulnerabilities and misconfigurations through automated remediation workflows. Build custom workflows to respond to specific exposures using a visual and intuitive workflow builder.

Absolute Randomware Response
Boost ransomware preparedness and receive guidance from the Absolute Professional Services team to respond effectively when an incident occurs. Assess your security posture, identify and remediate the health of your endpoint management and security applications, provide tailored communication to end-users and freeze devices to limit the spread of infection.
Secure Access

Absolute Core
Resilient Zero Trust Network Access with dynamic policy enforcement and Network Access Control (NAC) for always-on secure connections to public and private applications regardless of the user’s location.

Absolute Edge
Includes all the functionality in Absolute Core and adds in-line CASB, Digital Experience Monitoring (DEM) and Network Performance Diagnostics and Management (NPMD), and AI- and ML-powered proactive threat notifications for organizations that need more visibility and security.

Absolute Enterprise
Includes all the functionality in Absolute Edge and adds comprehensive Secure Web Gateway (SWG) capabilities including multiple AV scans, Remote Browser Isolation (RBI), Content Disarm and Reconstruction (CDR), Data Loss Prevention (DLP), and Endpoint Compliance for complete visibility and security for today’s modern workforce.
Stop Downtime in Minutes, Not Hours or Days
- Firmware-embedded persistence
- Automated OS image recovery
- Remote remediation at scale without delay
- Business continutiy without disruption
Try Absolute Rehydrate in your own Environment
Prove It, No-Cost Trial. Maximum Savings.
Experience how Absolute Rehydrate swiftly restores endpoints, reduces recovery expenses, and delivers measurable ROI across your remote and hybrid workforce.


IT Security Teams Love Absolute
Over 18,000 companies rely on Absolute to manage and secure their endpoint environments.
Email us or call us at (02) 9388 1741.
Solutions Offered
Explore our wide range of cutting-edge technologies.
Secure Access Service Edge (SASE) is a cloud-delivered framework that converges essential networking and security functions into a unified platform.
